Introduction
In today's digital landscape, where online privacy is increasingly important and access restrictions are more sophisticated than ever, mobile proxies have emerged as a powerful solution for businesses and individuals alike. As the most advanced proxy type currently available, mobile proxies provide unparalleled legitimacy and access capabilities that other proxy types simply cannot match.
This comprehensive guide explores mobile proxies in depth—what they are, how they work, their advantages over other proxy types, and the specific use cases where they excel. Whether you're involved in market research, social media management, ad verification, or app testing, understanding mobile proxies can give you a significant competitive advantage.
What Are Mobile Proxies?
Mobile proxies are intermediary servers that route your internet traffic through mobile devices connected to cellular networks (4G/5G/LTE). Unlike datacenter or residential proxies, mobile proxies use IP addresses assigned by mobile carriers to real mobile devices, making them the most legitimate and least detectable proxy type available.
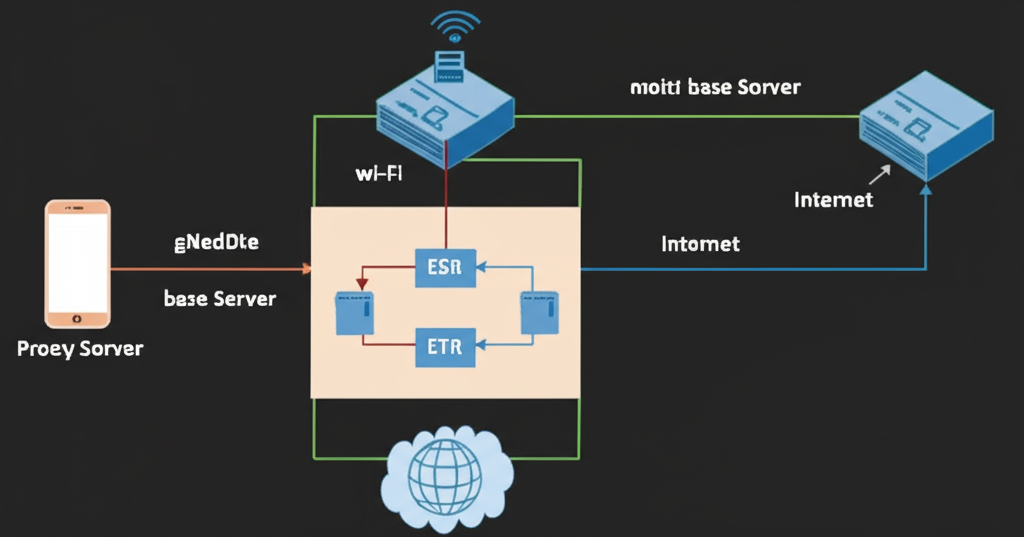
When you connect to the internet through a mobile proxy, your traffic appears to come from a genuine mobile device on a cellular network. This provides several key advantages:
- •Highest Legitimacy: Mobile IPs are considered the most trustworthy by websites and platforms since they come from real mobile carriers.
- •Rotating IPs: Many mobile proxy services offer automatic IP rotation as mobile devices naturally change IPs when moving between cell towers.
- •Geo-targeting: Mobile proxies can provide access from specific countries or regions, allowing you to view content as users from those locations would.
- •Bypass Restrictions: They excel at accessing platforms with strict anti-bot and anti-proxy measures, such as social media sites and e-commerce platforms.
How Mobile Proxies Work
Understanding how mobile proxies function requires knowledge of both proxy technology and mobile network infrastructure. Here's a breakdown of the technical process:
- 1Mobile Device Network:
Mobile proxies utilize a network of real smartphones, tablets, or mobile hotspots connected to cellular data networks (4G/LTE/5G). These tablets, or mobile hotspots connected to cellular data networks (4G/LTE/5G). These devices are either dedicated proxy devices or part of a device farm where users have opted to share their connection.
- 2Proxy Server Infrastructure:
The proxy provider maintains servers that connect to these mobile devices. When you send a request, it first goes to these proxy servers, which then route it through the mobile devices.
- 3Traffic Routing:
Your web request travels from your device to the proxy provider's server, then through the mobile device, out to the internet via the cellular network, and back through the same path to return to you.
- 4IP Assignment:
The destination website sees the request coming from the mobile device's IP address, which is assigned by a mobile carrier like Verizon, AT&T, T-Mobile, or their international equivalents.
- 5Natural IP Rotation:
Mobile carriers frequently reassign IP addresses as devices move between cell towers or reconnect to the network. This creates a natural rotation of IPs that adds another layer of anonymity.
Mobile Proxy Sourcing Methods
Mobile proxies are sourced through several different methods:
- •Dedicated Device Farms: Some providers maintain their own networks of mobile devices specifically for proxy services.
- •P2P Networks: Users install apps that share their mobile connection in exchange for compensation or services.
- •SIM Card Farms: Large collections of SIM cards in specialized devices that connect to mobile networks.
- •Mobile Gateways: Enterprise-grade solutions that maintain multiple carrier connections.
Mobile vs. Other Proxy Types
To understand the unique value of mobile proxies, it's important to compare them with other common proxy types: datacenter and residential proxies.
Mobile vs. Datacenter Proxies
| Feature | Mobile Proxies | Datacenter Proxies |
|---|---|---|
| Source | Mobile carriers (4G/5G networks) | Data centers and cloud providers |
| Detection Risk | Very low | High |
| Speed | Moderate (depends on cellular connection) | Very fast |
| Cost | High | Low |
| IP Diversity | High (constantly changing IPs) | Limited (easily identified as datacenter IPs) |
| Success with Restricted Sites | Very high | Low |
Key Difference: Mobile proxies provide authentic mobile carrier IP addresses that are rarely flagged or blocked, while datacenter proxies are easily identified as non-residential IPs and frequently blocked by sophisticated websites.
Mobile vs. Residential Proxies
| Feature | Mobile Proxies | Residential Proxies |
|---|---|---|
| Source | Mobile carriers (4G/5G networks) | Home ISPs (cable, DSL, fiber) |
| Detection Risk | Very low | Low |
| Speed | Moderate (depends on cellular connection) | Moderate to fast (depends on home connection) |
| Cost | High | Medium to high |
| Natural IP Rotation | Frequent (as devices move between cell towers) | Less frequent (typically when modems reconnect) |
| Success with Social Media | Excellent | Good |
Key Difference: While both mobile and residential proxies use legitimate consumer IP addresses, mobile proxies have an edge for platforms that prioritize mobile users or have stricter security measures. Mobile IPs also rotate more naturally and frequently than residential IPs.
Advantages of Mobile Proxies
Mobile proxies offer several distinct advantages that make them the preferred choice for certain applications:
Highest Legitimacy
Mobile IPs are considered the most legitimate type of proxy because they come from real mobile carriers and are used by millions of genuine mobile users. This makes them extremely difficult to detect as proxies.
Superior Access to Restricted Platforms
Mobile proxies excel at accessing platforms with sophisticated anti-bot and anti-proxy measures, such as social media sites, sneaker sites, and ticket vendors.
Natural IP Rotation
Mobile IPs change naturally as devices move between cell towers or reconnect to the network, providing built-in rotation that appears completely organic to target websites.
Mobile User Emulation
For businesses targeting mobile users, mobile proxies allow you to see exactly what mobile users see, including mobile-specific content, pricing, and features.
Geo-targeting Precision
Mobile proxies can provide highly accurate geo-targeting, allowing access from specific countries, regions, or even cities, which is valuable for localized market research.
Lower Ban Rates
Websites and platforms are much less likely to block mobile IPs, resulting in higher success rates for activities like web scraping, account creation, and automated tasks.
Limitations and Challenges
Despite their advantages, mobile proxies do have some limitations that should be considered:
Higher Cost
Mobile proxies are typically the most expensive proxy type due to the costs associated with maintaining mobile connections and devices. Expect to pay significantly more compared to datacenter or even residential proxies.
Variable Speed and Stability
Mobile connections can be less stable and slower than fixed-line connections. Performance may vary based on network congestion, signal strength, and carrier quality in different regions.
Limited Bandwidth
Mobile data plans often have bandwidth limitations, which can restrict the volume of data that can be processed through mobile proxies. This makes them less suitable for extremely high-volume operations.
Smaller IP Pools
The pool of available mobile IPs is typically smaller than datacenter or residential proxy pools, which can be a limitation for very large-scale operations requiring many unique IPs.
Ethical Considerations
Some mobile proxy networks operate by using bandwidth from users who may not fully understand how their connection is being used. It's important to choose providers with transparent and ethical sourcing practices.
Key Use Cases
Mobile proxies excel in specific use cases where their unique advantages provide significant benefits:
Social Media Management
Social media platforms have some of the most sophisticated systems for detecting and blocking proxy usage. Mobile proxies are particularly valuable for:
Social Media Applications:
- Managing multiple social media accounts without triggering security flags
- Automating actions like posting, following, and engagement
- Accessing geo-restricted content or features
- Creating and verifying new accounts without blocks
- Viewing social media ads as they appear to users in different locations
Ad Verification
For businesses investing in digital advertising, verifying how ads appear to users in different locations is crucial:
Ad Verification Applications:
- Confirming ads appear correctly on mobile devices in target markets
- Checking competitor ad placements across different regions
- Verifying geo-targeted ad campaigns reach the right audiences
- Monitoring for ad fraud by viewing ads as genuine mobile users
- Testing mobile-specific ad formats and displays
Market Research
Mobile proxies provide valuable insights for businesses conducting market research:
Market Research Applications:
- Collecting accurate pricing data from different regions
- Monitoring product availability and promotions in various markets
- Gathering mobile-specific search results and recommendations
- Analyzing competitor strategies across different geographic areas
- Accessing region-restricted content and services
Mobile App Testing
For mobile app developers and QA teams, mobile proxies offer unique testing capabilities:
App Testing Applications:
- Testing app performance across different mobile carriers
- Verifying geo-restricted features work correctly in target markets
- Ensuring apps function properly under various network conditions
- Testing location-based services and features
- Validating in-app purchase systems across regions
How to Choose a Mobile Proxy Provider
Selecting the right mobile proxy provider is crucial for success. Here are the key factors to consider:
| Factor | What to Look For |
|---|---|
| IP Pool Size | Larger pools provide more unique IPs and better coverage. Check the number of IPs available in your target regions. |
| Geographic Coverage | Ensure the provider offers coverage in all your target countries and regions. Some providers excel in specific areas. |
| Carrier Diversity | Ensure the provider offers a diverse range of carriers in your target regions. This reduces the risk of blocks and provides more reliable access. |
| IP Rotation Options | Look for providers that offer both automatic IP rotation and the ability to request new IPs on demand. |
| Connection Speed and Stability | Test the connection speed and stability of the proxies before committing to a long-term plan. |
| Authentication Methods | Providers should offer multiple authentication methods, such as username/password and IP whitelisting. |
| Customer Support | Choose a provider with responsive and knowledgeable customer support to assist with any issues. |
| Pricing and Plans | Compare pricing models (e.g., bandwidth-based, port-based) and choose a plan that aligns with your usage requirements. |
| Ethical Sourcing | Inquire about the provider's sourcing methods to ensure they are ethical and transparent. Avoid providers that use deceptive or exploitative practices. |
Setup and Configuration
Configuring mobile proxies typically involves the following steps:
- 1Account Setup:
Create an account with your chosen mobile proxy provider and select a suitable plan.
- 2Authentication:
Configure authentication using either username/password or IP whitelisting, depending on the provider's options.
- 3Proxy Settings:
Set up your applications or browsers to use the proxy server address and port provided by the proxy service.
- 4Geo-targeting (Optional):
If you need to target specific locations, configure the proxy settings to use IPs from those regions.
- 5Testing:
Verify that the proxy is working correctly by checking your IP address and location through a website like WhatIsMyIPAddress.com.
Best Practices
To maximize the effectiveness and minimize the risks associated with mobile proxies, follow these best practices:
- •Rotate IPs Regularly: Even though mobile IPs rotate naturally, it's still a good idea to rotate them periodically to further reduce detection risks.
- •Use Appropriate User Agents: Set user agents to match the type of mobile device you are emulating to appear more legitimate.
- •Limit Concurrent Connections: Avoid making too many simultaneous requests from the same IP address, as this can trigger security alerts.
- •Monitor Bandwidth Usage: Keep track of your bandwidth consumption to avoid exceeding your plan limits.
- •Choose Reputable Providers: Select providers with a proven track record of reliability, ethical sourcing practices, and strong security measures.
- •Stay Informed: Keep up-to-date with the latest anti-proxy techniques and adjust your strategies accordingly.
Future Trends
The mobile proxy landscape is constantly evolving. Here are some trends to watch:
- •5G Adoption: As 5G networks become more widespread, mobile proxies will offer even faster speeds and lower latency.
- •AI-Powered Proxy Management: AI and machine learning will be used to optimize proxy rotation, detect and avoid blocks, and improve overall performance.
- •Decentralized Proxy Networks: Blockchain-based proxy networks will offer greater transparency, security, and control.
- •Enhanced Geo-targeting: Mobile proxies will offer even more granular geo-targeting capabilities, allowing businesses to target specific neighborhoods or even individual buildings.
- •Integration with IoT Devices: Mobile proxies will be used to secure and manage IoT devices in various applications, such as smart cities and industrial automation.
Conclusion
Mobile proxies are a powerful tool for businesses and individuals who need the highest level of legitimacy, access, and control over their online activities. While they come with certain limitations and challenges, their unique advantages make them the preferred choice for a wide range of use cases, from social media management to market research to mobile app testing. By understanding how mobile proxies work, their advantages and limitations, and how to choose the right provider, you can leverage this technology to achieve your goals and stay ahead of the curve in today's increasingly complex digital landscape.
Written by FindProxy.org Research Team
Proxy Technology Experts
